"Fishstickz" And The Phishing Of John Podesta
Campaign IT worker at center of hacking drama

![]()
NOVEMBER 7--In a campaign marked by talk of pussy grabbing, “bleached” e-mails, Mexican rapists, and the continuing escapades of Carlos Danger, why shouldn’t a gamer known as “Fishstickz” play a role in possibly deciding the next president of the United States?
A month after her April 2015 presidential announcement, Hillary Clinton arrived at her campaign headquarters for an inaugural tour and introduction to the mostly young staffers working in the downtown Brooklyn office.
After making brief remarks about how it was “important to have fun” while also winning the Democratic nomination, Clinton, with aide Huma Abedin in tow, moved through the space that May morning shaking hands and posing for individual photos and group shots.
The headquarters was dotted with ceiling signs indicating which shops--policy, communications, digital, etc.--were grouped where in the open-plan space. Along with the name of the department, the signs each carried a humorous kicker, like “A decision tree grows in Brooklyn” for the analytics staff or “It depends” for legal.
The campaign’s information technology staff worked under a sign declaring, “We’ll do IT live,” the words Bill O’Reilly once famously yelled during an anchor desk meltdown on the set of the tabloid show “Inside Edition.” As the IT staff gathered for a team photo with Clinton (seen above), the campaign’s chief information officer, Shane Hable, stood at the candidate’s right shoulder, while Asad Yousof, a systems engineer, was to Clinton’s left. Next to Yousof was Charles Delavan, the help desk manager.
Owing to Big Data, analytics, and the online nature of modern campaigns, the Clinton IT department was particularly important. The operation reported to Stephanie Hannon, the campaign’s chief technology officer. Hannon, a veteran Silicon Valley executive, was hired away from Google and tasked with overseeing a platoon of engineers, software developers, and consultants.
Along with creating web sites, apps, and other methods to connect with prospective voters and donors, Hannon’s team was also responsible for establishing and maintaining security measures to handle all manner of cyberthreats directed at the Clinton campaign.
As detailed earlier this year in a Politico story, the work of Hannon, Hable, and lead security engineer Tim Ball “includes daily internal security audits.” The trio was also responsible for “briefings for campaign staff on ‘social engineering’ threats like phishing emails.”
Politico’s piece about the Clinton campaign’s in-house security efforts was published on March 31. By then, however, it was already too late.
* * *
Beginning on October 7, Wikileaks began posting the fruits of a criminal plundering of the Gmail account of John Podesta, the Clinton campaign chairman. To date, the site has published in excess of 55,000 Podesta e-mails in 33 (and counting) separate tranches. The initial release of Podesta e-mails came hours after the publication of a recording in which Donald Trump boasted about forcibly kissing and groping women.
The daily release of Podesta e-mails sets off a mad scramble by Clinton detractors to locate what they perceive to be the latest incriminating correspondence. The resulting storm of tweets and reports in conservative and alt-right  publications often wildly mischaracterize Podesta e-mails, all in the service of furthering narratives about Clinton corruption, the screwing of poor Bernie Sanders, and even Podesta’s purported interest in satanic-themed dinners (to which he does not apparently bring his creamy risotto).
publications often wildly mischaracterize Podesta e-mails, all in the service of furthering narratives about Clinton corruption, the screwing of poor Bernie Sanders, and even Podesta’s purported interest in satanic-themed dinners (to which he does not apparently bring his creamy risotto).
The Podesta e-mails have been embraced by the Trump campaign, which has been invigorated by the daily Wikileaks dumps. That purloined material has also been a programming bonanza for Fox News, where Sean Hannity, Trump’s shameless signal booster, has reconsidered his opinion of Assange, whose arrest Hannity once demanded for “waging war against the U.S..”
Which is not to say that the Podesta e-mails amount to a “nothingburger,” as some Clinton supporters have claimed. The correspondence highlights the Democratic presidential nominee’s coziness with Wall Street, the knotty conflict of interest and fundraising questions surrounding the Clinton Foundation, and the related issue of the lucrative for-profit activities of “Bill Clinton, Inc.”
So far, Wikleaks has published 55,694 Podesta e-mails, some of which date back more than a decade. But what Julian Assange & Co. have not published during their month-long fencing of stolen goods is the original e-mail that was sent by hackers to Podesta (and which resulted in the breach of his Gmail account).
As TSG reported last month, on the morning of March 19, a Saturday, Podesta received an e-mail that appeared to come from the Google address “[email protected].” The e-mail’s subject line declared that, “Someone has your password.” The e-mail itself reported a sign-in attempt from an IP address in Ukraine, a bid that Google purportedly thwarted. “You should change your password immediately,” suggested “The Gmail Team.” To facilitate that security update, the e-mail included a blue “CHANGE PASSWORD” box just waiting to be clicked.
By now, everyone knows that the e-mail to Podesta was part of a large, coordinated effort to hack into the personal e-mail accounts of hundreds of individuals, many of whom 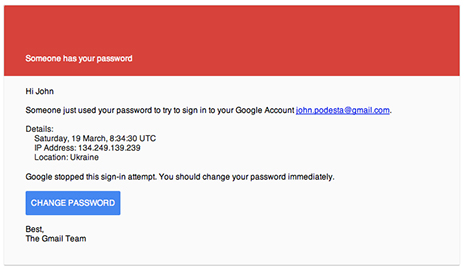 work for either the Clinton campaign or the Democratic National Committee.
work for either the Clinton campaign or the Democratic National Committee.
And despite Donald Trump’s contention that the hacking campaign--which has lasted more than 18 months--could have been orchestrated by a 400-pound couch potato (or just about any country short of Vatican City), there appears little doubt that Russian intelligence agents have carried out the illegal operation. Or that the hackers intended to influence or disrupt the U.S. presidential election. The Podesta e-mails, stolen in late-March, were shelved for seven months before they began appearing on Wikileaks just a month before Election Day.
Based on what has been distributed via Wikileaks, the DC Leaks web site, and self-described “hacktivist” “Guccifer 2.0,” the Russian operation succeeded in breaching the DNC’s computer systems and the e-mails of Podesta and several low-level Clinton campaign staffers handling organizing, press, and advance team responsibilities. But those hacked records also yielded hundreds of other potential Gmail addresses to be targeted with the kind of “spear phishing” e-mail that was sent to Podesta and the other victims.
Owners of Gmail accounts that were likely similarly targeted by the hackers include top Clinton campaign officials like Robby Mook, Jennifer Palmieri, Cheryl Mills, Tony Carrk, Jake Sullivan, and Brian Fallon. Others whose personal Gmail addresses were available to the hackers included Senator Elizabeth Warren; New York City Mayor Bill DeBlasio; Chicago Mayor Rahm Emanuel; former Clinton aide Sidney Blumenthal; Democratic strategist David Axelrod; Neera Tanden, president of the Center for American Progress; and Doug Band, Bill Clinton’s former personal assistant.
Seen above, the weaponized e-mail that was sent to Podesta arrived in his Gmail inbox at 4:34 AM. While it is unclear who first opened the e-mail, Podesta’s chief of staff, Sara Latham, forwarded it around 9:30 AM to Charles Delavan, the IT department’s help desk manager.

Delavan, 28, was hired by the campaign in the weeks before Clinton’s formal announcement. He moved to Brooklyn from Washington, D.C., where he had worked for the DNC and The MIS Department, a technology firm that had provided services to the DNC and both of Barack Obama’s presidential campaigns. Delavan reported to Shane Hable, the campaign’s chief information officer, with whom he worked at the DNC and the MIS firm.
An Annapolis, Maryland native, Delavan studied computer science at the Rochester Intitute of Technology for a couple of years before eventually graduating in May 2012 with a political science degree from the University of Maryland, Baltimore County.
Like many of his peers, Delavan is a gamer and a member of the Steam online community. Known by the handle “Fishstickz,” Delavan is an eGames enthusiast particulary devoted to Dota 2, a multiplayer battle game. In a July 2014 Facebook post, Delavan reminded his friends that the grand finals of a $5 million Dota 2 tournament were underway and he included a link to a “great noob stream” about “this thing I love so much.” Delavan’s social media accounts have also included photos chronicling his interest in craft beers.
While with the DNC, Delavan worked the 2012 Democratic National Convention and was later detailed to Obama’s Chicago headquarters for the final weeks of the presidential campaign. Delavan was in the crowd of staffers when a teary  Obama offered them his thanks the day after his reelection.
Obama offered them his thanks the day after his reelection.
On the Sunday Clinton announced her candidacy, Delavan took to Twitter to let his followers know that he had “moved up to Brooklyn to start working on the IT Team for Hillary For America. It’s exciting and and awesome!” In a follow-up tweet, Delavan wrote, “I can’t wait for all the stuff to come!”
When Delavan (pictured at right) received the e-mail forwarded to him by Podesta’s chief aide on March 19, he could not have imagined the repercussions of his actions that morning. While the original e-mail to Podesta has not surfaced in the Wikleaks collection, it is included in a chain that was part of a late-October release.
After examining the e-mail, Delavan wrote back to Latham and Hable and flatly declared that the purported communication from Google “is a legitimate email.” He added that Podesta needed to change his password immediately and enable two-factor authorization on his Gmail account. Delavan’s e-mail included a text link to the actual Google page where Podesta’s account could be updated.
Latham then forwarded Delavan’s e-mail to Milia Fisher, a Podesta assistant who replied that she would immediately call the campaign chairman “and work on new passwords.” It appears that Fisher or Podesta did not follow the password change link provided by Delavan, but instead clicked on the “CHANGE PASSWORD” button in the original e-mail.
Delavan has not returned TSG texts or phone message seeking comment, so it is unclear why he thought the e-mail to Podesta was “legitimate.” But it seems likely that his examination of the e-mail did not go beyond the fact that it looked real and appeared to have been sent from the googlemail.com domain.
Had Delavan--or any other campaign worker--simply examined the message’s header, they would have realized that the e-mail actually came from Yandex.com, a Moscow-based e-mail provider. A further examination of the e-mail’s full header would have revealed that, when clicked, the “CHANGE PASSWORD” button directed a user to a computer in the Netherlands (which carried a web address with the .tk country domain for Tokelau).
But that never happened, and Delavan unintentionally helped facilitate the ransacking of Podesta’s account and the resulting damaging drip, drip, drip via Wikileaks.
* * *
By all accounts, Delavan has been an exemplary worker for the Clinton campaign, one of the many twentysomethings who have logged long hours for more than 18 months. According to the campaign’s most recent Federal Election Commission filing, Delavan’s last reported bi-weekly payroll check was for $2413.13.
Delavan has had contact with virtually every campaign employee, if only by e-mail. Upon being hired by Hillary for America, a staffer received a Delavan-authored welcome message “from the IT Team!”
Along with providing the help desk’s e-mail address and phone number, Delavan instructed new hires on how to set up their campaign e-mail account (HFA has relied on a Google Apps mail server, which allows the campaign to use Gmail as its e-mail solution). In his introductory note, Delavan stressed the importance of security: “Two-step authentication for your account is required by the campaign, and failure to do so will result in an inability to access your account.”
Delavan also suggested creating passwords with a minimum of 12 characters (“including one lower case letter, upper case letter, symbol, and number”). He then added, “Please do not share your password with anyone! (Not even us. Nobody. Not ever.)”
To underscore his security message, Delavan linked the words “Not even us. Nobody. Not ever.” to the below animated gif of Finn the Human, a character from Cartoon Network’s “Adventure Time” series, yelling “Never!” (1 page)





